You Validate Your Downloaded Software, Right?
Do you validate your downloaded software's hash? Avoid potential pitfalls and keep yourself secure with these useful tips and tricks.
How many applications have you downloaded in the past year? How many times did you bother to follow the full instructions and verify the downloaded software wasn't modified in transit? Not many, if at all is my guess.
Most of the time when someone downloads a new application, they are in a hurry and just want it installed so that they can get on with whatever task they were doing. People have busy lives and don't have the extra time to squander on unimportant topics like security and privacy. "If it works, it works!"
Those of you out there that have fallen victim to identify theft and credit card fraud might feel a little different. In 2020, according to the FTC’s Consumer Sentinel Network Data Book, the most prevalent fraud complaints were debt collection, imposter scams, and identity theft. In the identity theft category, credit card fraud was highest with 167,000+ people reporting that a phony credit card account was opened using their personal information.
So is there anything you can do besides setting up a reputable anti-virus software and praying to your god of choice?
A Good Defense
One line of defense you can take is to verify that the software you download onto your machine is actually what it claims to be. On certain software download pages you will see something like this:
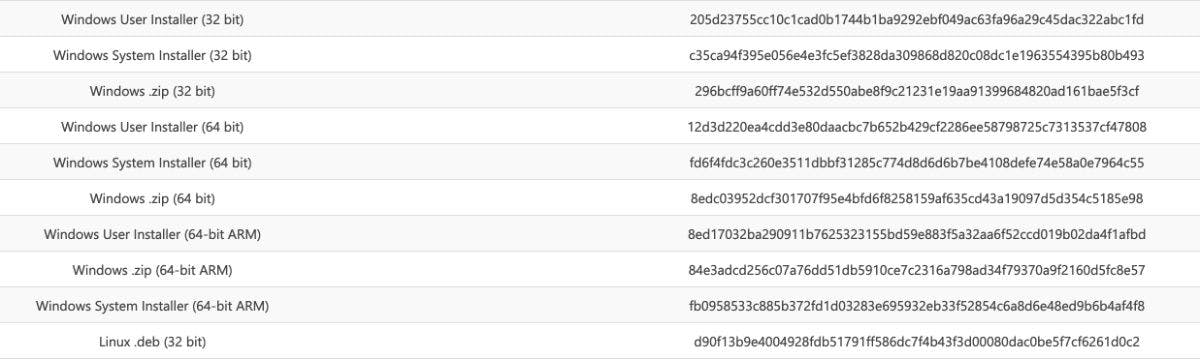
These are computer hashes of the software packages themself. These hashes are derived from a one-way algorithm, so they are often used for hashing passwords. These hashes are stored in the database which hides the actual password if the database is ever breached. This is assuming the password is long enough that the hash cannot be brute forced.
This lets the user run the hash command on the downloaded software package. If the resulting hash matches the one on the website, then you can confirm that your downloaded software has not be altered by any middlemen.
The Middleman
One such example is that of Kazakhstan.
In 2015, the government of Kazakhstan created a root certificate which could have allowed such an attack on HTTPS traffic internet users. It was described by the Kazakh government as a "national security certificate", and if installed on the devices of unsuspecting users, it would allow the government to intercept, decrypt, and re-encrypt any traffic.
Luckily in 2019, Google and Firefox browsers advised that they would not accept the certificate - even if manually installed by users.
So let's get down to business. Here are some commands you can run to increase the odds that you are downloading what you think you are. With the generated hash you can compare it with the one listed on the website.
Windows
To find the SHA256 checksum use the following command in the command line:
certutil -hashfile /path/to/file SHA256
Here is an example using the previous command:
certutil -hashfile ~/Downloads/WebStorm-2021.1.3.dmg SHA256
Which results in:
3011d8188e473fdeba49abcdfaf408c15e41ed34283f67b80144793de4e82ba1 WebStorm-2017.1.3.dmg
There is many other hashing algorithms, some of which have become outdated (MD5 + SHA1), you can substitute these values in the command itself.
Another easy way to find the hash of a file is to use the Windows 10 Power Shell.
First open the Windows Powershell application (click “Start” then type “Powershell” then hit enter), then use the command below. Ensure to fill in the relevant details instead of "YourUsername" and "filename.exe".
Get-FileHash -Path c:\Users\YourUsername\Desktop\filename.exe -Algorithm SHA256.
Mac
To find the SHA256 checksum use the following command in the terminal:
shasum -a 256 /path/to/file
Here is an example using the previous command:
shasum -a 256 ~/Downloads/WebStorm-2021.1.3.dmg
Which results in:
3011d8188e473fdeba49abcdfaf408c15e41ed34283f67b80144793de4e82ba1 WebStorm-2017.1.3.dmg
There is many other hashing algorithms, some of which have become outdated (MD5 + SHA1), you can see the full list here:
MD5
md5 ~/Downloads/<placeholder>.dmg
MD5 (OpenSSL)
openssl md5 ~/Downloads/<placeholder>.dmg
SHA1
shasum -a 1 ~/Downloads/<placeholder>.dmg
SHA1 (OpenSSL)
openssl sha1 ~/Downloads/<placeholder>.dmg
SHA256
shasum -a 256 ~/Downloads/<placeholder>.dmg
SHA256 (OpenSSL)
openssl sha256 ~/Downloads/<placeholder>.dmg
SHA512
shasum -a 512 ~/Downloads/<placeholder>.dmg
SHA512 (OpenSSL)
openssl sha512 ~/Downloads/<placeholder>.dmg
The Hacked Server
There's always a chance too that the website in which you downloaded the software from was hacked. This can be tricky as the software you download might match with the provided hash code on the website, as hackers could have changed it.
So how can this be avoided? Some tactics include:
- Following the social media pages of the software teams so that you can mitigate any problems as fast as possible when they arise.
- Only downloading stable releases, not the nightly releases as they can contain security holes.
- Only downloading reputable software. Do some research online to see if they have a following and genuine reviews.
- Checking online to see if the software has a history of security breaches.
- Only using software within walled gardens such as the Google & Apple stores.
- Deleting old software that is not supported anymore. Adobe Flash is still on millions of machines, even though it is not supported and has serious security flaws. Thankfully modern browers have removed it completely.
Final Thoughts
One of the best and easiest ways to know if you have been hacked, is to see if your details have already been breached and sold online. You can even sign up to be notified if your details appear in a new data breach.
haveibeenpwned.com is a great tool to start with, and can tell you if your email/password has appeared in online breaches. Last, but not least, remember to never use the same password for more than one service. Stay safe out there on the internet highway!
You can check out my blog to keep updated with my latest posts! Jotcode Blog

